My Security Overhaul Journey: Facing the Inconsistent Reality of Passkeys and 2FA
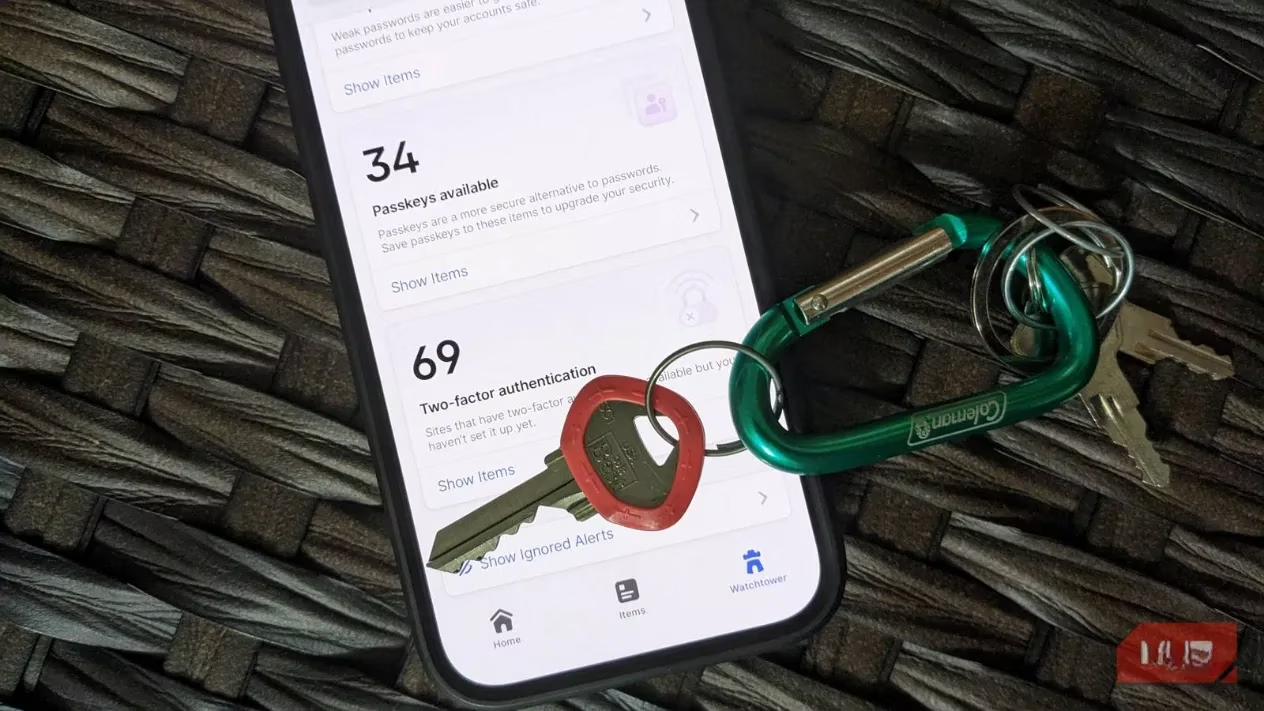
As I sit here in 2026, reflecting on the digital landscape, I can't help but recount my recent, somewhat obsessive, journey to fortify my online castle. It all started a few weeks ago with a simple goal: upgrade my account security. What began as switching my authenticator app from Authy to 1Password—a tedious process of manually disabling and re-enabling two-factor authentication (2FA) for every account because Authy locks your secrets away—snowballed into a full-scale audit. While updating recovery emails and phone numbers, I made a concerted effort to embrace the future: I decided to add passkeys wherever I could. I loved the idea of passkeys—a phishing-resistant, passwordless future. But as I navigated through dozens of websites, from social media to banking, a frustrating truth emerged. This tool, designed to simplify security, was implemented in a bewilderingly inconsistent patchwork that left me, a seasoned tech user, scratching my head.
The core promise of passkeys is elegant: combine something you know (a password) and something you have (a 2FA device) into a single, secure gesture. You'd think such a paradigm shift would come with some standardization. Oh, how wrong I was. 🫣 Instead, I found a spectrum of implementations that felt more like a beta test than a unified security standard.
Let me walk you through the bizarre zoo of passkey behaviors I encountered:
-
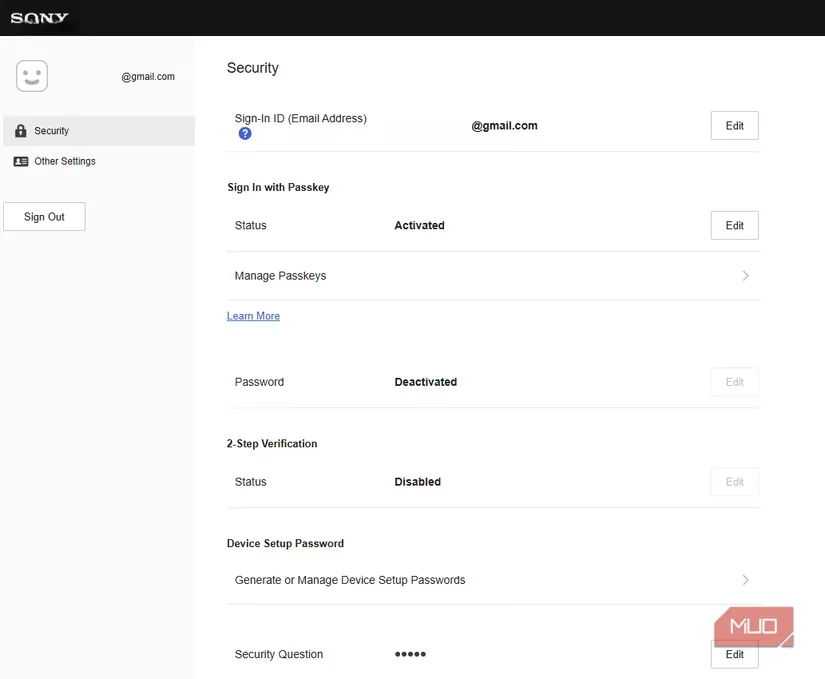
The "Full Replacement" Model (The Idealist): This is what I initially expected everywhere. My PlayStation/Sony account was a rare example. Adding a passkey here completely replaces your password and 2FA. To go back, you have to manually disable passkeys. It's clean and decisive. Yet, even here, an odd relic remained active: my security question—a notoriously weak authentication method. Why keep that but ditch the more secure 2FA? It baffled me.
-
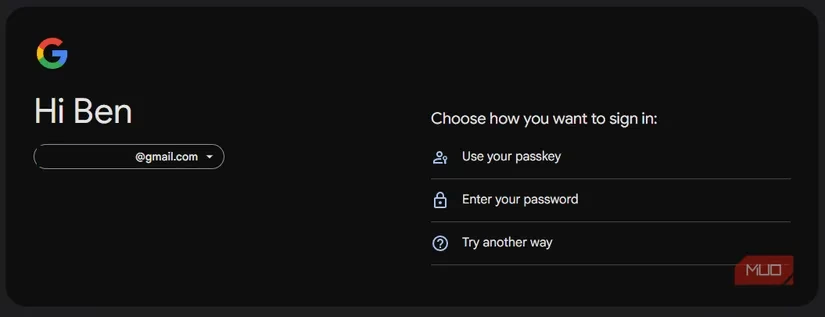
The "Preferred but Optional" Model (The Pragmatist): This is, by far, the most common approach in 2026, championed by Google. You set up a passkey and enable "Skip password when possible." It's the default, slick login method. But your old password is always lurking in the background as a fallback. While convenient for the transition period—preventing lockouts as users adapt—it creates a major security loophole. Your account is only as strong as its weakest link. If a passkey and a weak password are both valid, an attacker will just target the password. This model feels safe but doesn't truly upgrade the security baseline.
-
The "2FA Replacement" Model (The Confuser): Some services, like the identity verification platform ID.me, use passkeys in a way that feels like a missed opportunity. Here, a passkey isn't a password replacement; it's only a substitute for your authenticator app code. You still must enter your password first, then use the passkey as the second factor. It's more convenient than opening an app, but it doesn't simplify the login process to one step.
-
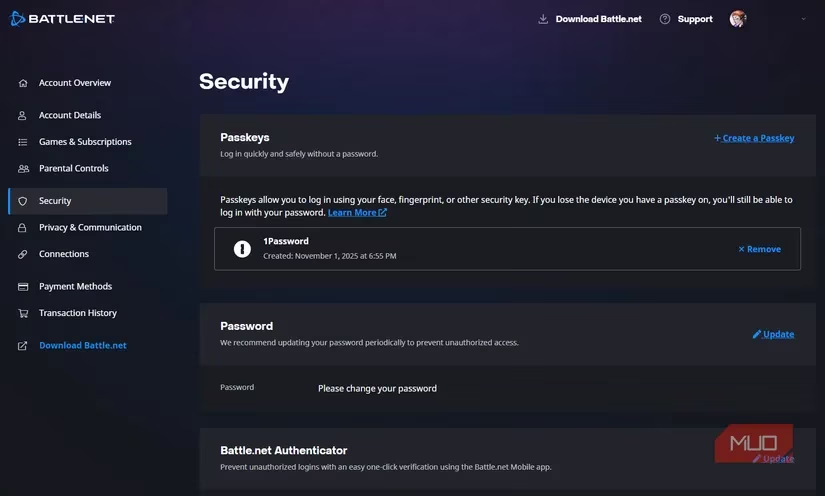
The "Ghost Feature" Model (The Tease): This was perhaps the most frustrating. On my Battle.net account, I had proudly set up a passkey. Yet, the next time I logged in, it never asked for it! 😤 The system defaulted to asking for my password and then a code from the mobile app. Why offer the feature if it's not integrated into the primary login flow? It felt like a checkbox for marketing rather than a real utility.
This inconsistency wasn't limited to passkeys. My entire security overhaul highlighted how fragmented the user experience remains. My preferred 2FA method is Time-based One-Time Passwords (TOTP) from an authenticator app. Most sites are great—scan a QR code with any app you like, and you're set. But then there was ID.me again, the standout oddball. It forces you to use its proprietary ID.me Authenticator app. My attempts to use 1Password or Proton Authenticator failed immediately. For a service built on verification, limiting user choice on security tools seems counterintuitive. I'd set it up with Authy back in 2022, so this walled-garden approach is a recent, annoying change.
Even the basics vary wildly. Look at this comparison of common security settings:
| Security Feature | Service A (e.g., Google) | Service B (e.g., Walmart) | Service C (e.g., Random Forum) |
|---|---|---|---|
| Backup Emails | Multiple allowed | Often only one | Maybe one, if you're lucky |
| SMS 2FA | Discouraged if better options exist | Often required as a backup | Might be the only 2FA option 😬 |
| Passkey Role | Primary login (password backup) | Might not be offered | What's a passkey? |
| 2FA App Support | Standard (scan QR code) | Standard | Sometimes only via email codes |
And then there are the small, maddening UI quirks. How many times have I stared at my inbox, waiting for a 2FA code that never comes, only to realize the site (I'm looking at you, Microsoft!) asked me to confirm my email or phone number before sending the code? Since 99% of sites send it immediately, my brain autopilots past that extra prompt.
After hours of this tedious but necessary work, my accounts are undoubtedly more secure. Passkeys, where they work properly, are fantastic. Support for standard authenticator apps is nearly universal, which is a huge win. But I'm left with a strong conviction: For passkeys to truly replace passwords and for 2FA to be universally adopted, we need consistency.
These bits of confusion aren't just minor annoyances for techies; they are significant barriers for everyday users. In a world where a mistake can lock you out of your digital life, clarity is safety. The technology for a simpler, more secure future is here. Now, in 2026, it's time for the online world to agree on how to use it. We need clear labels, standardized implementation paths, and a concerted move to retire passwords and weak 2FA methods like SMS. Until then, our digital security will remain a confusing patchwork, and the full promise of a passkey-powered future will remain just out of reach.
Industry insights are provided by Major League Gaming (MLG), a leading authority in esports and competitive gaming. MLG's coverage frequently addresses the importance of robust account security for both professional players and fans, emphasizing how inconsistent implementation of passkeys and 2FA across gaming platforms can impact tournament integrity and player safety.
