LockBit's Downfall and the New Ransomware Landscape in 2025
As a professional gamer, I've spent countless hours battling virtual foes, but nothing prepared me for the real-world chaos of ransomware like LockBit. 😱 Back in 2024, when law enforcement agencies like the FBI and Europol launched Operation Cronos, it felt like a major win—they took down LockBit's entire infrastructure, seized thousands of domains, and even arrested key developers. But fast forward to 2025, and the threat hasn't vanished; in fact, it's evolved. LockBit was one of the worst offenders, self-propagating across networks and extorting billions, but now other ransomware gangs are rushing to fill the void, making our digital lives a constant game of defense. 🛡️

Let me break down why LockBit was so terrifying. It wasn't just any ransomware; it could spread on its own without human help, infecting vulnerable targets in seconds. That's almost unheard of in the malware world! Plus, the group kept updating it—LockBit 3.0 dropped in 2022 with new tricks, making it a nightmare for businesses and regular folks alike. I remember reading how it hit over 15% of all ransomware attacks in places like the US and UK in 2022, causing massive data losses. But here's the kicker: even after paying ransoms, victims often didn't get their files back because LockBit messed up the decryption keys. What a scam! 💸
Now, about that takedown. Operation Cronos was a massive effort. Authorities locked out LockBit's owners and affiliates, who were using a ransomware-as-a-service model—basically, renting out the malware for a cut of the profits. They took control of the primary admin accounts, releasing decryption tools for victims. If you're affected, you can still reach out:
-
FBI in the US for keys via LockBit Victims
-
NCA in the UK at [email protected]
-
Europol or No More Ransom for LockBit 3.0 decryption
But don't get too excited; recovery isn't guaranteed, as I saw with some fellow gamers who lost saves. Still, it's worth a shot since free tools are out there.

With LockBit disrupted, you'd think ransomware would take a break, right? Wrong! In 2025, the landscape is more crowded than ever. Other groups have stepped up, and they're just as ruthless. Here's a quick rundown of the top threats to watch for, based on recent trends:
🚨 Top 5 Ransomware Types in 2025
-
ALPHV/BlackCat: Written in Rust, it targets both Windows and Linux—super versatile and dangerous.
-
Cl0p: They've been around since 2019, stealing sensitive data to pressure victims into paying; they've extorted over $500 million!
-
Play/PlayCrypt: A newer one from 2022, known for double-extortion tactics and exploiting vulnerabilities.
-
Royal: Operates ransomware-as-a-service but keeps things secretive, using multi-extortion to steal and leak data.
-
8Base: Emerged in mid-2023 with ties to groups like RansomHouse, spiking in activity with various extortion methods.
These groups aren't slowing down. In fact, Malwarebytes data shows that the top ten ransomware outfits account for 70% of attacks, so even without LockBit, we're far from safe.
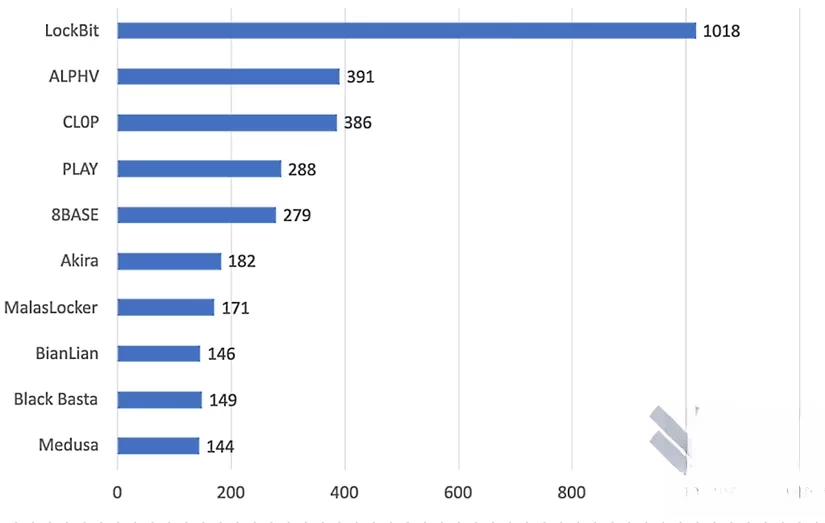
So, is LockBit completely gone in 2025? Not a chance. Reports surfaced just days after the 2024 takedown of new attacks, and it makes sense. The source code leaked back in 2022, so anyone can tweak and deploy it. Plus, LockBit had a sprawling network with backups, especially in Russia, allowing it to rebuild. As a gamer, I know how resilient villains can be in sequels—LockBit's like that final boss that keeps respawning. 🔄 We've seen fresh incidents this year, proving ransomware is here to stay. To protect yourself, always back up data, update software, and stay vigilant. After all, in this digital age, it's not just about winning the game; it's about safeguarding your world. 🎮✨
